Last Updated on 2 years ago by Imarticus Learning
Data breach in 2022: Introduction to incident management in cybersecurity
To put it simply, a data breach refers to any incident involving the theft of information from a system without the knowledge or authorization of the system’s owner. In recent years, cybersecurity breaches have multiplied like never before! Be it large or small companies, there’s hardly any sector that is not vulnerable to cybercrime.
The latest incidents of high-profile attacks targeting a wide spectrum of sectors, including healthcare, finance, retail, government, manufacturing, and energy, have compelled industry insiders to sit up and take notice of the threat landscape. Going by expert projections, cybercrime is expected to cost the global economy $10.5 trillion by 2025, alarming to even mammoth businesses.
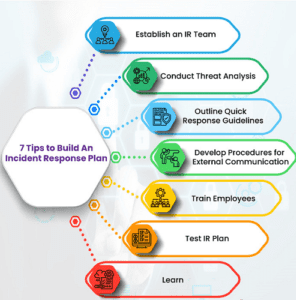 Incident management in cybersecurity implies the process of identifying, managing, recording, and analyzing the security, threats, and incidents associated with cybersecurity.
Incident management in cybersecurity implies the process of identifying, managing, recording, and analyzing the security, threats, and incidents associated with cybersecurity.
It is a crucial step that immediately follows or precedes a cyber disaster in an IT infrastructure. Incident management in cybersecurity requires a significant degree of knowledge and experience.
With efficient incident management in place, you can considerably minimize the adverse impact of cyber destruction, besides keeping cyber-attacks at bay.
What’s more, it also prevents data leaks. An organization without a good incident response plan might fall prey to cyberattacks, which can lead to major compromises with the data of the organization.
The following steps are involved in incident management in cybersecurity:
- The first step involves an alert that reports an incident that has occurred. This is followed by the engagement of the incident response team, which prepares itself to tackle the incident.
- Next comes identifying potential security incidents by monitoring and reporting all incidents.
- Based on the outcome of the previous step, the next step is responding to the incident by containing, investigating, and resolving it.
- Finally, every incident should be documented with its learnings and key takeaways.
Also, check out the following tips for security incident management:
- It is imperative for every organization to ensure a mature and fool-proof incident management process that implements the best practices for a comprehensive plan.
- Make sure your incident management plan is equipped with supporting policies that include well-laid-out guidance on the detection, reporting, assessment, and response of the incidents. A checklist should be prepared, putting down the actions based on the threat. The incident management plan should also be continuously updated as per requirement, especially with regard to lessons learned from previous incidents.
- Creating an Incident Response Team (IRT) plays an instrumental role in working on clearly defined goals and responsibilities. It will also be entrusted with functional roles such as finance, legal, communication, and operations.
- Incident management procedures can go quite a few notches higher with regular information security training and mock drills. These go a long way in boosting the IRT’s functionality and keeping them on their toes.
- A post-incident analysis after any security incident can make a considerable difference in teaching you a thing or two about successes and failures. This helps a lot in making necessary adjustments to the program and incident management processes as and when required.
What More You Need
In incident management in cybersecurity, collecting evidence and analyzing forensics is always highly recommended, which is an integral part of incident response. You need the following things for the same:
- A well-defined policy can effectively assimilate evidence while ensuring its accuracy and sufficiency to be admissible in a court of law.
- The incident response should be such that it can employ forensics as required for analysis, reporting, and investigation.
- The IRT personnel must be well-trained in cyber forensics and functional techniques. They should also have some knowledge of legal and governance issues. You can visit our training centers in Mumbai, Thane, Pune, Chennai, Bengaluru, Delhi, and Gurgaon for cybersecurity training online.
In a nutshell, a robust incident management process can reduce your recovery costs and potential liabilities and, above all, minimize the damage to the victim, not only at a personal level but also at the organizational level.
If you’re looking for cyber security training online, contact us through chat support.



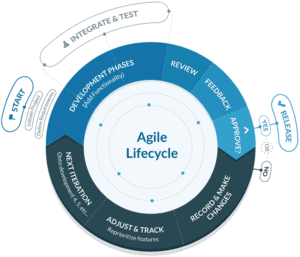 Analogously, agile hiring is aimed at being more cognizant of the needs of the organization and making the process more efficient.
Analogously, agile hiring is aimed at being more cognizant of the needs of the organization and making the process more efficient.