Cybersecurity is a term you hear often, but what does it really mean, and more importantly, what does cybersecurity protect?
In a recent KPMG survey of 500 CEOs, 18% said that cybersecurity risks would be the biggest threat to their company’s growth. This is an increase from 10% last year. Whether you’re a business owner, a student, or just someone using the internet, understanding cybersecurity is essential.
Let’s dive into the various aspects of cybersecurity, why it’s crucial, and how it shields our digital world.
What is Cyber security?
Cybersecurity is the term encompassing the procedures and tools used to defend networks, systems, and data against cyberattacks, which can take many different forms, from hacking attempts to data breaches and other cyber threats. Essentially, cybersecurity is the digital shield that guards against unauthorized access and damage to your digital assets.
Cyber security involves using technology, strategies, and practices to prevent or lessen the impact of cyberattacks. It aims to protect individuals and organizations’ systems, applications, devices, sensitive data, and financial assets from threats like viruses and costly ransomware attacks.
Cyberattacks can disrupt, damage, or destroy businesses, with the costs to victims continually increasing. These trends offer significant business benefits and human progress but also create more opportunities for cybercriminals to exploit.
Security teams, often stretched thin, are focusing on developing comprehensive cybersecurity strategies using advanced analytics, artificial intelligence, and automation to combat cyber threats more effectively and reduce the impact of cyberattacks.
Types of Cybersecurity (Cybersecurity Domains)
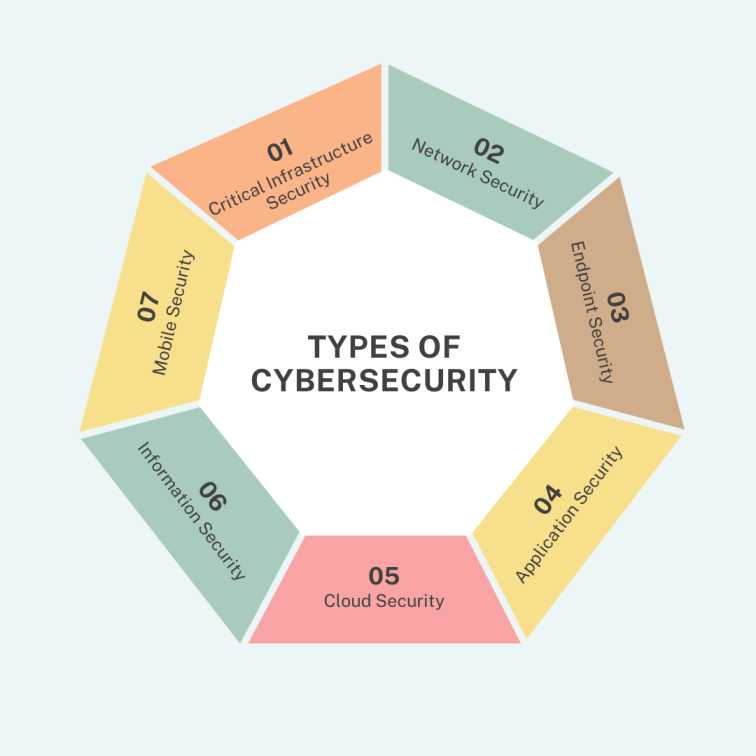
A strong cybersecurity strategy protects all parts of your IT setup against cyber threats and cybercrime. Here are the main areas it covers:
-
Critical Infrastructure Security
This protects the essential computer systems, applications, networks, and data that society relies on for national security, economic health, and public safety. In the U.S., the National Institute of Standards & Technology has created a cybersecurity framework to guide IT providers. The Cybersecurity and Infrastructure Security Agency also offers additional guidance.
-
Network Security
Network security stops unauthorized access to network resources and detects and prevents cyberattacks. It also ensures that authorized users can access the resources they need securely and quickly.
-
Endpoint Security
Endpoints like servers, desktops, laptops, and mobile devices are common entry points for cyberattacks. Endpoint security protects these devices & their users from attacks and also safeguards the network from threats originating from these endpoints.
-
Application Security
Application security protects programs running both on-premises and in the cloud. It prevents unauthorized access to applications and their data and also stops hackers from exploiting design flaws. Modern development practices like DevOps and DevSecOps include security measures from the start of the development process.
-
Cloud Security
Cloud security protects an organization’s cloud-based services and assets, such as applications, data, storage, and virtual servers. Cloud security follows a shared responsibility model: the cloud provider secures the services and infrastructure, while the customer protects their data and other assets in the cloud. The specifics can vary depending on the cloud services used.
-
Information Security
Information security involves protecting all important information—whether digital files, paper documents, physical media, or even spoken words—from unauthorized access, use, or changes. Data security, which focuses on protecting digital information, is a key part of InfoSec and the main focus of cybersecurity efforts.
-
Mobile Security
Mobile security includes various technologies and practices to protect smartphones and mobile devices. This can include mobile application management (MAM) and enterprise mobility management (EMM). Recently, mobile security is often part of unified endpoint management (UEM) solutions, which manage and secure multiple devices (mobile, desktops, laptops) from a single platform.
What Does Cybersecurity Protect?
Now, let’s delve into the core question: what does cybersecurity protect?
Here are the main areas cybersecurity aims to safeguard:
-
Personal Data
Personal data includes any information that can identify you as an individual, such as your name, address, Social Security number, or financial details. Cybersecurity measures protect this sensitive information from being accessed, stolen, or misused by malicious actors.
-
Financial Information
Financial data, including credit card numbers, bank account details, and transaction records, are prime targets for cybercriminals. Cybersecurity helps protect this information from being stolen, ensuring that your finances remain secure.
-
Intellectual Property
Protecting intellectual property such as patents, trade secrets, & proprietary information is crucial. Cybersecurity measures prevent competitors and hackers from accessing and exploiting this valuable information.
-
Operational Data
This includes any data related to the day-to-day operations of a business, such as client lists, supply chain information, and internal communications. Cybersecurity ensures that these operations run smoothly without interruptions from cyber attacks.
-
Government and Military Information
National security depends heavily on cybersecurity to protect sensitive government and military information. Unauthorized access to this data could have difficult consequences for a country’s safety and stability.
What are the Common Cyber Threats?
Understanding what cyber security protects also involves knowing the types of threats it guards against. Here are some common cyber threats:
-
Malware
Malware, or malicious software, includes viruses, worms, trojans, and spyware. These malicious programs can steal, encrypt, or delete sensitive data, disrupt operations, and more.
-
Phishing
Phishing attacks utilize deceptive emails, texts, or websites to deceive people into divulging private information like credit card numbers, usernames, or passwords.
-
Ransomware
A type of malware that encrypts a victim’s data and demands payment (ransom) for the decryption key. This can cause significant disruptions and financial loss.
-
Denial of Service (DoS) Attacks
DoS attacks aim to overwhelm a system, server, or network, rendering it unavailable to users. This can severely impact business operations and services.
Analysts specializing in cybersecurity are essential in defending companies from online attacks. They assess security concerns, keep an eye out for network breaches, and create plans to fend off cyberattacks.
The Final Words
In a period where digital threats loom large, cybersecurity stands as the frontline defender of our personal and professional lives. By safeguarding personal data, financial information, intellectual property, and critical infrastructure, cybersecurity ensures the smooth functioning of our interconnected world.
As cyber threats evolve, staying informed and vigilant is crucial. By understanding and implementing robust cybersecurity measures, we can protect our digital assets and contribute to a safer digital landscape for everyone.
Advanced Certificate In Cybersecurity & Blockchain With E&ICT Academy IIT Guwahati
Imarticus Learning, in collaboration with E&ICT Academy IIT Guwahati, offers an Advanced Certificate in Cybersecurity and Blockchain. This cyber security analyst course delves into the dynamic worlds of cybersecurity, cryptography, and blockchain, mirroring industry practices. The curriculum is your roadmap to mastering critical skills & preparing you for a secure and innovative future.
A cyber security analyst course is designed to equip individuals with the knowledge & skills needed to identify, prevent, and respond to cyber threats. These courses cover various topics, including network security, ethical hacking, cryptography, and risk management. By taking such a course, individuals can prepare for a career in the growing field of cybersecurity.
The curriculum developed by IIT Guwahati professors and industry experts concentrates on networking principles, ethical hacking, vulnerability analysis, blockchain, and general network security. Participate in immersive, hands-on lab sessions & learn to utilize tools such as VMware, Kali OS, Wireshark, Nessus, Nmap, and more. This practical experience demonstrates your proficiency in cybersecurity techniques and methodologies.
Take the next step in your cybersecurity career with Imarticus Learning’s Advanced Certificate in Cybersecurity and Blockchain. Arm yourself with the know-how to defend against online attacks, utilize encryption to secure data, and discover how blockchain is revolutionizing a number of industries.
Enrol now and secure your future in the dynamic world of cybersecurity!

