The Chief Financial Officer (CFO) role has come a long way. No longer mere guardian of numbers, today’s CFO is a key strategic business partner, a digital disruptor champion, and a driver of business expansion and value creation. For a senior finance manager hoping to vie for this strategic C-suite role, choosing the right Chief Financial Officer Course is vital.
Of all the different executive finance courses and executive finance programmes on offer, the Indian School of Business (ISB) Chief Financial Officer (CFO) Programme always stands out. This blog delves into why the programme has its place and whether or not it really does deliver on what senior professionals expect in achieving financial leadership.
The Strategic Imperative: Why a Dedicated CFO Course?
For veteran finance professionals, merely piling on years of experience might no longer guarantee the transition to the CFO position. Today’s CFO must possess a unique combination of profound financial expertise, strategic vision, technical savvy, and outstanding leadership ability. A focused Chief Financial Officer Course delivers this specific training.
The ISB CFO Programme is specifically crafted for this shift. It transcends the conventional finance roles to prepare participants to:
- Anticipate Market Shifts: Identify financial opportunities and risks proactively.
- Drive Value Creation: Drive overall business strategy, rather than report on it.
- Lead Digital Transformation: Drive the adoption of the latest technology within finance.
The programme provides a holistic foundation that readies one for the diverse challenges of the CFO office. It is leadership training for CFOs, the best choice for individuals looking for a senior management course India has to offer for finance leaders.
Curriculum Excellence: What the ISB CFO Programme Covers
ISB’s Chief Financial Officer Course curriculum is carefully designed to equip participants with a comprehensive knowledge of modern-day financial leadership. The course allows for easy integration of sophisticated principles of finance with strategic choice and effective leadership development.
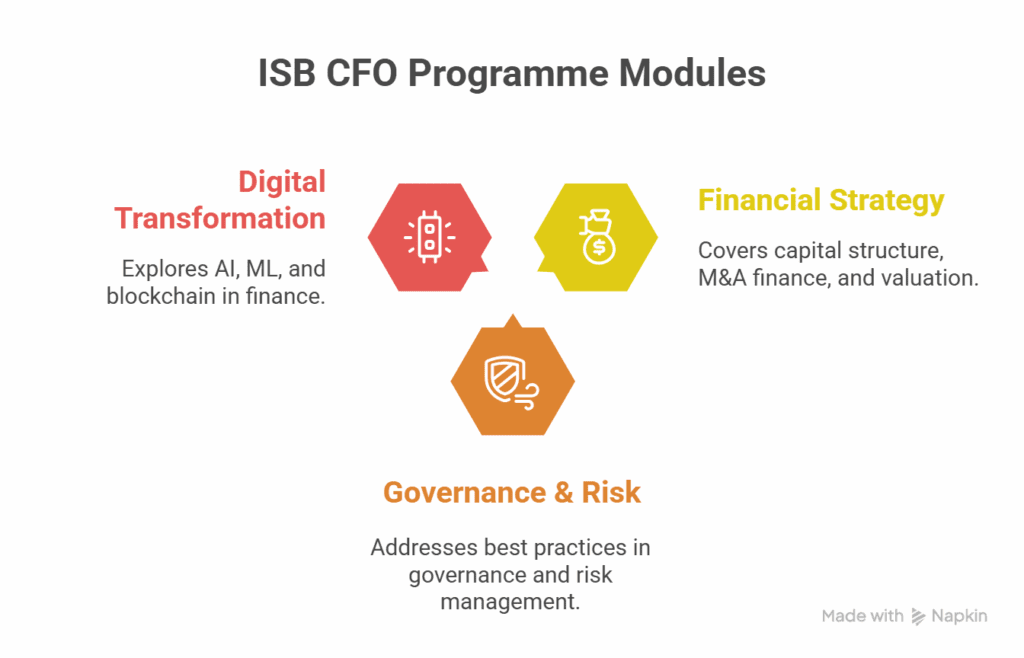
The main modules and subjects typically include:
- Financial Strategy & Capital Markets: This module covers advanced topics such as capital structure maximisation, M&A finance, and valuation techniques. It’s made to enable participants to make smart fundraising, investment, and overall performance decisions.
- Corporate Governance & Risk Management: As the business landscape continues to become increasingly regulated and risky, the programme comprehensively addresses best practices in corporate governance, enterprise risk management, and compliance regulation. This is significant when managing complex financial terrains.
- Digital Finance Transformation: One of the most significant facilitators for today’s CFO, this module explores how new technologies such as Artificial Intelligence (AI), Machine Learning (ML), and blockchain can be used to automate finance, improve data analytics, and enhance the power of prediction. Its emphasis on gazing into the future prepares participants with an awareness of what awaits the world of finance in 2025.
The future-oriented design of the programme enables participants to shift successfully from being mere financial specialists to strategic business partners.
Learning at its Best
Executive education at ISB stands out by focusing on practical learning, and the ISB CFO programme is no exception. It relies heavily on the learning experience via a case study method, exposing participants to real-world business issues. This method is more than passive learning since it requires active engagement and critical thinking.
Participants are requested to:
- Analyse Complex Situations: Tear apart comprehensive financial reports, market data, and company scenarios.
- Develop Strategic Recommendations: Develop and suggest sound financial plans, investment decisions, or risk management strategies.
- Engage in Rigorous Debates: Debate and defend their analysis and recommendations with peers and faculty, mimicking real boardroom discussions.
This practical application of knowledge is crucial for the development of decision-making abilities required in a CFO role. It ensures that the learning is not merely theoretical but also firmly grounded and directly applicable to work problems, thus making it an extremely beneficial finance leadership programme.
Aseem, a Chief Financial Officer with years of experience, shares his journey of the ISB CFO Programme.
Networking and Community: ISB Advantage
Aside from the curriculum, the Chief Financial Officer Course by ISB has perhaps one of the best opportunities for networking in the industry.
The course gathers a group of highly experienced finance experts who are part of the following:
- Controllers and Financial Directors
- Treasurers and Risk Managers
- Entrepreneurs with significant financial control
- Finance consultants
This experience diversity enhances class discussions and offers rich peer-to-peer learning. Discussing intricate financial matters with peers from diverse industries and backgrounds creates a well-rounded perspective and develops firm professional relationships.
In addition, members become part of the highly regarded and large ISB alumni network. The network is a strong tool for career development, providing mentorship, industry knowledge, and future prospects. Alumni testimonials always praise the strength of the ISB network as a “goldmine of contacts” and as an important factor in career development for individuals with an ISB CFO certification.
Career Impact: Ascending to the CFO Position
For mature professionals, the payback from an Executive Programme is in terms of concrete career advancement and improved leadership skill sets. ISB’s Chief Financial Officer programme is designed to help bring this acceleration about.
Alumni from these programmes typically report a dramatic turn in their career paths, including:
- Ascent to CFO or Deputy CFO jobs: The programme specifically gears them for these top jobs.
- Enlarged Mandates: Assuming wider strategic roles outside of classical finance, including M&A, digital transformation programs, and investor relations.
- Greater Earning Potential: Top executive positions naturally demand much higher pay packages. While individual salary hikes for this specific programme are not made public, the IIM executive programme 2025 results routinely record major salary increases. To put this in perspective, Indian CFOs (2025 salary guides) can negotiate salaries of ₹70 lakhs to more than ₹100 lakhs per year, depending on experience, firm size, and sector.
The programme provides finance professionals with the comprehensive skill set and strategic approach to impact business outcomes at the top level, making them in great demand for key financial leadership roles.
Table: Sample Career Path & Salary Potential (After-ISB Chief Financial Officer Course)
| Role Before Programme | Estimated Annual Salary Before (INR Lakhs) | Potential RoleAfter Programme | Estimated Annual Salary After (INR Lakhs) | Career Impact |
| Senior Finance Manager / Controller | ₹25 LPA – ₹45 LPA | VP Finance / Finance Director | ₹45 LPA – ₹75+ LPA | Enhanced strategic input & broader scope |
| Head of Finance /AVP Finance | ₹40 LPA – ₹70 LPA | Aspiring CFO / Deputy CFO | ₹70 LPA – ₹100+ LPA | Direct pathway to CFO roles, C-suite discussions |
| Experienced CFO (for update) | ₹60 LPA – ₹100+ LPA | More impactful / Strategic CFO | ₹90 LPA – ₹150+ LPA | Refined leadership, future-proofed skills |
Note: These numbers are indicative and according to general market trends for senior finance executive positions in India for 2025, taking into consideration results from ISB executive education and top management programs. Actual salaries may differ significantly depending on industry, company size, and personal performance.
Meeting Future Trends: The CFO of 2025 and Beyond
The CFO’s role is constantly changing due to technology, economic changes around the world, and mounting pressure for sustainability. The ISB Chief Financial Officer Course is updated regularly to meet these new trends so that participants can cope with the future.
Certain of the areas of future-proofing covered in the curriculum are:
- Data-Driven Decision Making: Emphasis on leveraging big data, AI, and machine learning for predictive analytics, sophisticated financial modelling, and strategic insights.
- ESG Integration: Understanding the impact of Environmental, Social, and Governance (ESG) considerations on financial performance, reporting, and long-term value creation. CFOs will be relied upon to be at the forefront of supporting sustainable finance initiatives.
- Digital Transformation Leadership: Not only should CFOs be leading digital initiatives in the finance organisation, but also throughout the entire organisation, driving automation, cloud deployment, and robust cybersecurity practices. This qualifies it as a bleeding-edge leadership development initiative for CFOs.
- Strategic Communication: Having the capacity to take complex financial data and convert it into easy, compelling narratives that engage a range of stakeholders (investors, board members, staff, regulators) is more crucial now than ever.
The programme will equip participants not only to master general management but to lead through innovation and ethics, so the programme is a cutting-edge finance leadership programme.
FAQs: Frequently Asked Questions Regarding the ISB CFO Programme
Most senior professionals and business leaders evaluating this course have some of these same questions. Here are some of the most common ones.
What is the work experience that is acceptable for the ISB Chief Financial Officer Course?
You know, when I first heard about the ISB CFO Programme, I figured it was for people who had been in the game for a long time. And I was right! It’s really for folks who are already pretty high up in their careers, especially in finance. We’re talking about people who have a solid decade, maybe even 12 years, of experience under their belts.
It’s not just about working in finance, though. They’re looking for people who have been in leadership roles-like if you’ve been a Finance Director, a Controller, or even a Treasurer. Someone who is driving innovation, business leaders, financial leaders, etc. It seems like the programme is really geared toward those who are either already in a top finance spot or are ready to jump into the CFO chair.
How does ISB CFO certification affect career advancement and pay in India?
From what I can gather, getting an ISB CFO certification is a massive deal, especially here in India. It’s like a golden ticket that tells everyone you’re not just good with numbers; you’re a strategic leader. While I can’t tell you the exact numbers, it seems like people who do this course see some pretty big changes.
It’s not just about getting a new job; it’s about moving straight up to those C-suite positions, like Group CFO. I’ve heard that the compensation jumps can be pretty wild, like a 50% increase or even more! It makes sense, right? A CFO’s role is so crucial, and with this certificate, you’re seen as someone who can handle those big, strategic decisions.
Is the ISB CFO course for full-time, or can one work while pursuing it?
That’s the best part! This course is made for people who are already working. I mean, it would be impossible for someone with 10+ years of experience to just quit their job, right? It’s a blended learning model, which is super flexible.
You do a lot of your work online, with live sessions, which is perfect for balancing with a job. The only time you’d need to take a break from your regular schedule is for a short campus visit. It’s a few days, maybe three to five, at the ISB campus. From what I hear, that part is a huge highlight because you get to meet everyone in person and really get into the material.
In what ways is this CFO programme different from a standard Executive MBA (EMBA)?
So, I was curious about this too. I always thought an EMBA was the ultimate executive programme. But this ISB CFO course is totally different. An EMBA is like a general business degree; it gives you a taste of everything-marketing, HR, operations, you name it.
This CFO course, though? It’s laser-focused on finance. It dives deep into all the nitty-gritty details of corporate finance, risk management, and capital markets. It’s not about being a manager in general; it’s about becoming a financial executive. It’s like it takes all the finance parts of a regular EMBA and just expands them to a whole new level.
What are the types of networking opportunities within this programme?
Oh, the networking is a big attraction for a programme like this. You’re in a group with other experienced finance professionals, so it’s not only about learning from the professors-it’s about learning from one another. Think of being in a virtual space with individuals who have battled through the same challenges that you have and successfully resolved them in unique ways. And then there’s the ISB alumni network.
It’s a huge, dominant community of individuals who are more than happy to assist one another. And they invite all these high-up executives in for guest lectures and masterclasses, so you’re basically able to rub shoulders with the best of the best. It feels like the networking you do is worth just as much as the classwork.
Does the programme address new trends such as AI, blockchain, and sustainability for CFOs?
I was really impressed to find out that this course isn’t just about old-school finance. It’s super modern. They’ve included all the new stuff that’s changing the business world. Things like how AI is affecting finance, how blockchain works, and even the importance of ESG and sustainability.
It’s clear they want to make sure that a CFO coming out of this programme isn’t just ready for today’s world but for tomorrow’s too. It’s not just a course; it’s a toolkit for the future, which is pretty awesome if you ask me.
The Value Proposition for Aspiring CFOs
The ISB Chief Financial Officer Programme offers a powerful value proposition for high-level professionals seeking the pinnacle of financial leadership. It goes beyond conventional finance education with a strategic, future-oriented curriculum that caters to the multifaceted needs of the contemporary CFO.
The intersection of world-class teaching faculty, an experiential pedagogy, and an extremely valuable professional network sets the participants up for a dramatic leap in career development. For those committed to building the financial future of their companies and willing to take the strategic responsibilities of a CFO, this Executive Programme at ISB creates a clear and effective path. The investment in this leadership programme in finance is an investment in becoming a truly indispensable strategic manager.
Are you ready to elevate your financial leadership?